Vetted on skills and experience.
The Cobalt vetting process is designed to ensure that our testers are the best and brightest crowd around. When inducting a researcher into the Cobalt Core, we look at a their skills, experience, and achievements in past security programs. This addition to the registration process ensures that only the best security researchers are active in Cobalt programs.
Undergo identity verification before receiving reward payments.
By law, we are required to keep a valid form of identification for each security researcher that receives payment through our platform. We know what you’re thinking — No, we did not suddenly become the NSA. We do this to be compliant, and to ensure that testers are paid for their bug bounty rewards as quickly as possible. We are committed to securely storing our tester data.
Profile Tips for Security Researchers
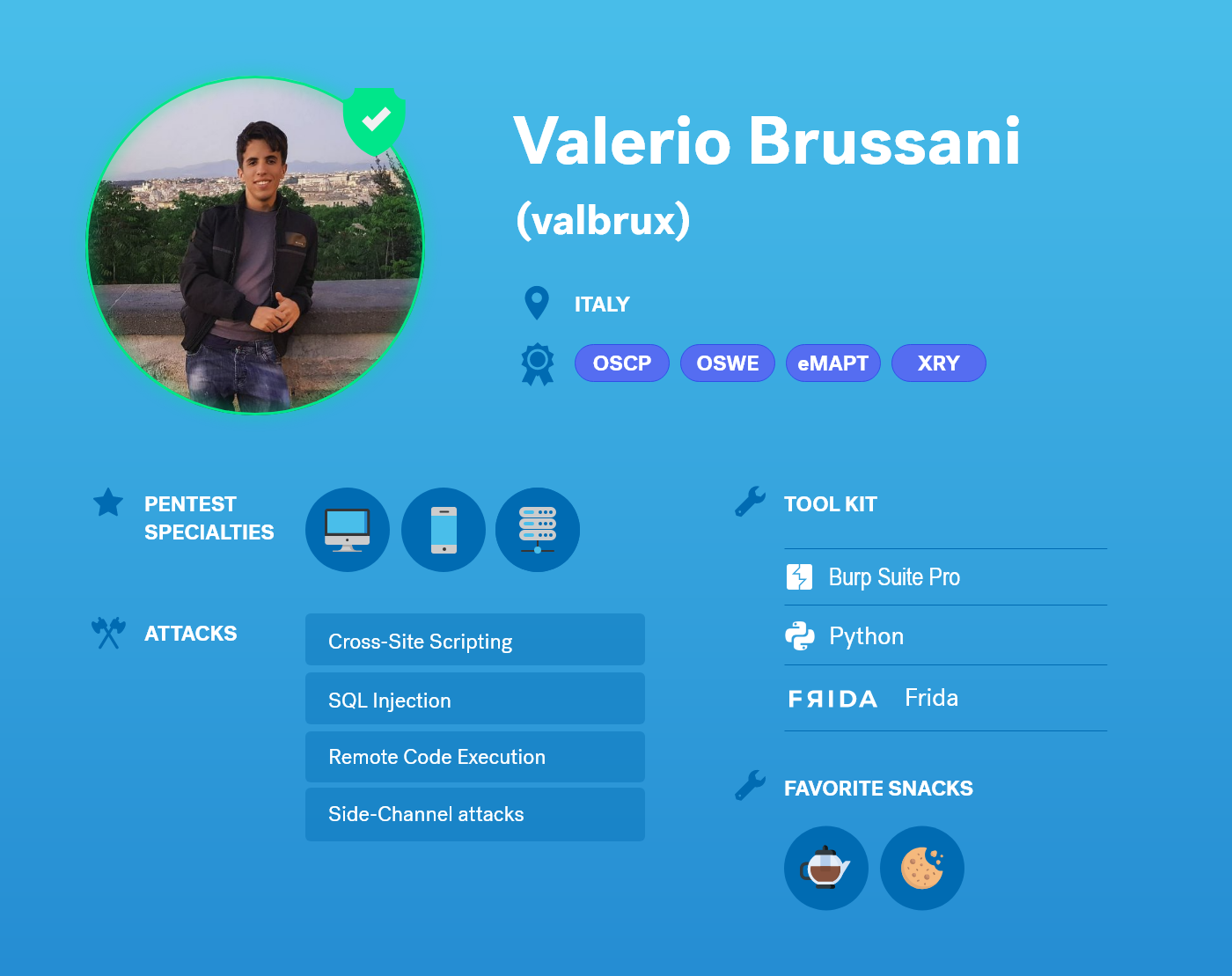
Your Cobalt profile is an important tool in building trust with businesses hosting bug bounty programs. All testers are encouraged to complete their tester profiles, which are visible to businesses and could potentially be showcased in our Hall of Fame.
-
Include as much information as possible about your background and accomplishments in security and web application testing.
-
Complete your profile by adding social network profiles, a strong profile image, and links to your work. (This will help speed up the vetting process)
-
We understand if you aren’t comfortable uploading your face on the internet — but avoid using cartoons, and offensive or violent images for your avatar.
-
Users with incomplete profiles or inappropriate profile images may have to wait longer for the vetting process to be complete.
We’ve instituted these changes to give both our researchers and businesses a positive experience on our platform. Do you have any questions or comments about these changes? Check out our FAQ or get in touch with us at hello@cobalt.io.